Automated Incident Response That Reduces Breach Impact
Automated Incident Response helps businesses detect threats fast, stop attacks, and reduce breach impact with quick actions and continuous monitoring.

Data breaches can happen at any moment. One wrong click, one weak password, or one unnoticed threat is enough for hackers to steal sensitive data. For businesses, this can mean financial loss, damage to reputation, and loss of customer trust.
Traditional manual security systems take time to detect and respond to threats. Even a small delay can give attackers enough time to access sensitive information. This is why many companies are now turning to AI Cyber Security to identify risks faster and reduce errors caused by manual work.
This is where Automated Incident Response becomes essential. It allows companies to react to threats instantly, stop attacks in progress, and reduce the impact of a breach.
What Is Automated Incident Response?
Automated Incident Response is a process where security systems automatically detect, analyze, and respond to cyber threats without waiting for human action.
Instead of relying on a human team to notice a breach, decide what to do, and then respond, automation handles these steps in seconds. This includes:
-
Detecting suspicious activity
-
Analyzing the severity of the threat
-
Containing the threat immediately
-
Alerting the security team
-
Recording the incident for future learning
The main goal is simple: stop threats quickly and reduce damage.
Why Breaches Cause So Much Damage
Data breaches are costly because:
-
Speed of attack: Hackers can steal data in minutes.
-
Human delay: Manual detection and response take hours or even days.
-
Human errors: Security teams can make mistakes under pressure.
-
Wider impact: A breach can affect multiple systems and users.
By the time a human team reacts, the attacker may already have caused serious damage. Security Automation Response solves this problem by acting instantly.
How Automated Incident Response Works
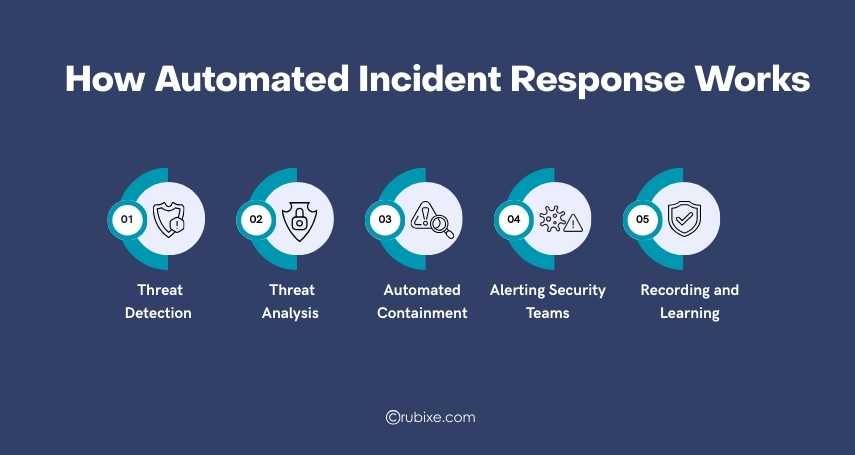
Automated Incident Response uses a combination of tools, AI, and pre-defined rules to protect systems. Here is a step-by-step explanation:
1. Threat Detection
Automated systems constantly monitor networks, servers, applications, and devices. They look for:
-
Unusual login attempts
-
Large or unexpected file transfers
-
Malware or ransomware activity
-
Suspicious connections or IP addresses
2. Threat Analysis
Once a potential threat is detected, the system evaluates it. Security Automation Response can:
-
Check the source of the threat
-
Compare it with known attack patterns
-
Determine the severity of the incident
-
Decide if immediate action is needed
3. Automated Containment
For high-risk threats, automated systems can take action immediately:
-
Block suspicious users or IP addresses
-
Quarantine infected files or devices
-
Stop data transfers
-
Disable compromised accounts
This reduces the time attackers have to access sensitive information.
4. Alerting Security Teams
Even though the system responds automatically, the human security team is notified. Alerts include:
-
What happened
-
Which systems were affected
-
Actions taken by the automated system
This allows the team to focus on strategy and prevention instead of rushing to contain the breach manually.
5. Recording and Learning
Every incident is logged and analyzed. Security Automation Response systems can:
-
Learn from attacks
-
Update detection rules
-
Improve future responses
This helps organizations get stronger over time.
Benefits of Automated Incident Response
Using Security Automation Response gives businesses several key benefits:
1. Faster Reaction Time
Modern Threats are detected and neutralized in seconds instead of hours. This minimizes the window of opportunity for hackers.
2. Reduced Breach Impact
Immediate containment stops the threat from spreading, protecting sensitive data and systems.
3. Lower Human Error
Automation reduces mistakes caused by delayed reactions or misjudgments under pressure.
4. Continuous Protection
Automated systems work 24/7, monitoring networks even when security teams are offline.
5. Cost Savings
By reducing the damage caused by breaches, companies save money on fines, legal costs, and recovery efforts.
6. Better Compliance
Automated logging and reporting help meet regulatory requirements for data protection and cybersecurity.
7. Enhanced Security Team Efficiency
Security teams can focus on strategy and complex threats while automation handles routine responses.
How Automated Incident Response Protects Businesses
Let’s take an example from a global financial services company.
The company noticed several unusual login attempts on their systems late at night. Normally, it would take hours for the human security team to investigate and respond.
But with Automated Incident Response:
-
The system immediately detected the suspicious logins
-
It temporarily blocked the accounts under attack
-
Alerted the security team with detailed information
-
Quarantined any files accessed during the breach attempt
As a result, the attack was stopped before any sensitive customer data was stolen. The company avoided major financial loss and reputational damage.
This example shows how automation can act faster than human response, making it a critical tool for businesses of all sizes.
Key Features of Automated Incident Response
Businesses should look for these features when implementing an automated response system:
-
24/7 monitoring: Continuous protection across all systems
-
AI and machine learning: Smarter detection and prediction of threats
-
Instant containment: Automatic blocking or quarantine of threats
-
Alerting and reporting: Clear notifications for human teams
-
Learning and updating: The system improves over time based on past incidents
-
Integration with existing systems: Works with firewalls, cloud platforms, and security software
-
Compliance support: Helps meet security regulations
Best Practices for Using Automated Incident Response
-
Define clear rules and thresholds
Set up policies for which threats should trigger automated actions.
-
Integrate with monitoring tools
Combine automation with SIEM (Security Information and Event Management) and other security tools.
-
Test regularly
Run simulations to ensure automated responses work correctly.
-
Keep humans in the loop
Automation handles quick responses, but human teams should review critical incidents.
-
Update detection rules frequently
Cyber threats change constantly, so the system should learn from new attack patterns.
Future Trends in Automated Security Responses
The field of automated security is growing quickly.
1. Smarter AI and Machine Learning
AI will become more intelligent at detecting unusual behavior. Automated systems will learn faster from past attacks and predict threats before they happen, making responses even quicker and more accurate.
2. Full Automation of Responses
In the future, more incidents will be handled automatically without waiting for human approval. This means threats will be contained instantly, reducing damage even more.
3. Integration Across Systems
Automated Incident Response will connect more deeply with different security tools, cloud platforms, and networks. This integration ensures that all systems work together to stop breaches effectively.
4. Predictive Threat Analysis
Automated systems will start predicting attacks by analyzing patterns, unusual activity, and historical data. This proactive approach helps prevent breaches before they occur.
Data breaches can happen at any time, and the speed of attacks makes manual response risky. Automated Incident Response helps businesses react instantly, contain threats, reduce the impact of breaches, and protect sensitive data.
By combining automation with smart monitoring, AI analysis, and instant alerts, companies can improve security, save costs, and keep customer trust intact. Automation is no longer just helpful, it is necessary to prevent serious damage from cyberattacks.
Investing in Automated Incident Response today is an important step toward safer, more secure business operations.